Synametrics Technologies
Revolving around the core of technology
Ransomware Prevention (RWP) with Syncrify
Tutorial Video
Watch a video on this topic- You have configured Syncrify to backup every night around 7 PM
- A ransomware hits around 4:45 PM on a Friday, fifteen minutes prior to close of business
- By 6:30 PM every important document is now encrypted
- A backup runs at 7 PM, which contaminates previously backed up data.
Important
RWP is designed to work when backup direction is either Client-to-Server or Two-way-sync. It does not work if the direction is Server-to-Client.How RWP works
Syncrify creates a dummy file, called a bait, in every top-level folder on the client's machine. This file get downloaded from your Syncrify Server and will have the same size and last modified date - meaning the copy on the client's machine will be identical to the copy on the server.Before backing up a top-level folder, Syncrify will match the file on the client matches with the copy on the server. An error gets logged if the file does not match, allowing the user to take corrective measures.
Tip
A bait file will be created in every top-level folder on the source machine.Configuring RWP
RWP is turned on by default. Syncrify server creates the bait file automatically by assigning a random file name. Administrators can change this name to give it a more meaningful touch. Following steps demonstrate how to do this:- Log in to Syncrify Server's web interface
- Click Configuration and select the Security tab
- Specify a file name for Ransomware File. This will be the name of your bait
- Create a file with the same name in put it in
$INSTALL_DIR/RansomwarePreventionfolder on the machine where Syncrify server is running. For example, create a file called RansomwareBait.docx using Microsoft Word and save it in theRansomwarePreventionfolder.
It is important to use a file extension that is typically targetted by ransomware viruses. For example, *.docx, *.jpg, *.xlsx and *.pdf are good examples. It is also recommended to write a message explaining your end-users the purpose of this file.
NOTE:$INSTALL_DIRrefers to the path where Syncrify Server is installed. On Windows, this is typicallyC:\Syncrifyand on Linux it is/opt/Syncrify
Disabling RWP
To disable this feature globally, remove the value for Ransomware File field in the Security tab of the Configuration screen. This will disable RWP for every client. The following image displays a screenshot.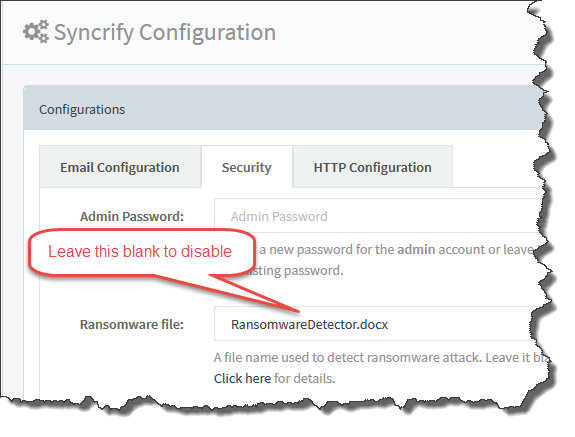
Disabling RWP for a single profile
Occasionally, you may want to disable RWP for a single profile. Following steps demonstrate how to do that.- Ensure a backup is NOT running currently
- Open Syncrify Client.
- Click Open Data Folder under File menu. This will open Windows File Explorer displaying the contents of the Data Folder.
- Locate
ProfileName.syncrify. This file contains information about your profile. Open this file in any editor, such as Notepad. - Search for the node
<ransomwareState>and change its value to 3. The line should look like following after modification:
<ransomwareState>3</ransomwareState>
- Save the file.
Resetting RWP
From the Client Side
Since the file created by RWP will be visible to the end-user, it is likely they may modify the file by mistake, triggering a false alarm. In that case, you must Reset RWP. To do that, open Syncrify Client and select Reset RWP under the Tools menu.From the Server Side
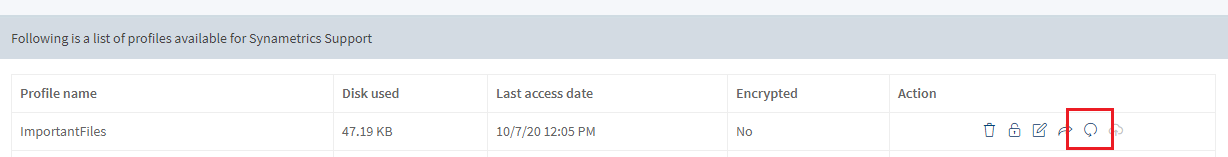
You can reset RWP for a specific profile from the admin console. To do this, follow these steps:- Go to your Manage Users page
- Click on View under the profiles column
- Click on the circle icon to reset RWP as shown below
Common Reasons For False Alarm
Consider the following reasons if a false alarm is triggered:- Reason 1: A user mistakenly modifies the file.
- Reason 2: The background service running Syncrify Client is unable to create the bait file. By default, the background service runs under the SYSTEM account. Depending upon the permissions on your machine, it is possible the operating system will not let the SYSTEM account create a file. A common folder this happens is user's Desktop, which is a considered a private folder and the operating system will not allow SYSTEM account to create a file. To fix, open Syncrify Client and click Reset RWP from the Tools menu. Then, run a full backup using the GUI (manual backup), which will create the bait file. Once the bait file is created, subsequent backups won't trigger the alert.
