Synametrics Technologies
Revolving around the core of technology
Is it dangerous to open port 80 for HTTP traffic?
Many administrators who manage web servers on their network tend to block traffic for port 80 (HTTP) and only allow 443 (HTTPS) with the hope that it will secure their network. This is a myth, and this article demonstrates why port 80 is no different than port 443 if your goal is to make your network secure.
Difference between HTTP and HTTPS
It is essential to understand what HTTPS offers in addition to HTTP. It offers two benefits:
- It encrypts data between the client (browser) and a web server, which means a third party, such as an ISP or an unauthorized individual, cannot view and modify the data.
- It ensures the server's identity. In other words, when you connect to your bank's website using a browser, HTTPS ensures you're connecting to your actual bank and not a malicious website that is trying to steal your credentials.
Notice the benefits mentioned above only secures the in-transit data between a browser and the web server. It does not change the security level of your server.
Can a Malicious User Attack an HTTP Server?
Yes. However, it is no different than attacking an HTTPS server. Anything someone can do to an HTTP server can also be done to an HTTPS server. Therefore, to say HTTP is more vulnerable than HTTPS is not correct. That said, you must treat HTTP and HTTPS equally to make your web server secure.
Disadvantages of Blocking Port 80
The following is a list of some disadvantages of blocking port 80.
- Often, users click on hyperlinks rather than typing them manually. Therefore, if the hyperlink on
the referrer's website uses HTTP, it cannot reach your website since the URL
http://your.website.comwill fail. - Although newer browsers will try HTTP and HTTPS when a user manually types an address, this functionality is browser-dependent. An older browser may not try looking for HTTPS, resulting in an error.
- Often, websites are fetched by computer programs and not a browser. In those cases, changes to the code or configuration file may be required to change every URL to HTTPS.
How to Configure Port 80
Rather than blocking port 80, consider redirecting its traffic to port 443, which forces the client to switch to HTTPS. The following sequence diagram displays the flow of events.
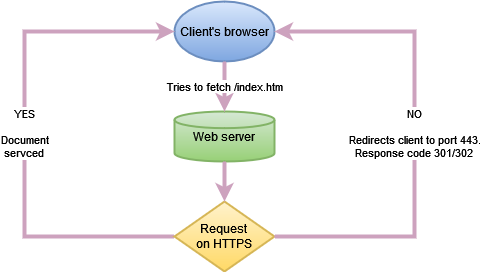
Example Configuration
As an example, let's see how Google configured their website. In this example, we will submit a request
to http://www.google.com and watch the communication between the browser and Google's web server.
We will use the Developer Tools that comes with Microsoft Edge browser to view the communication.
Here are the steps:
- Open MS Edge on your machine
- Press CTRL+SHIFT+I on your keyboard to bring up the Developer Tools
- Select the Network tab. Now you're ready to watch the communication between your browser and Google's web server.
- Type
http://www.google.comin the address bar. Ensure you type http:// in the beginning. - The following screenshot display the results:
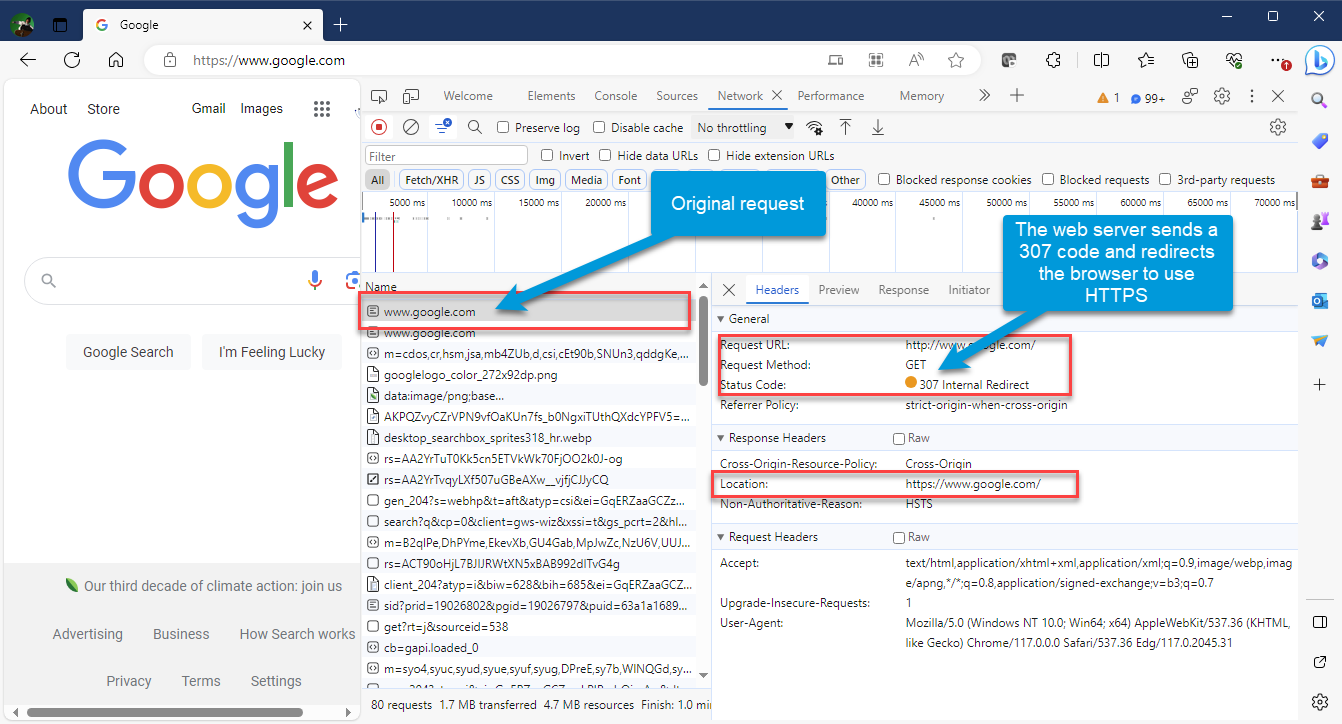
- Notice that Google's web server is listening an port 80 but instead of returning the document, it redirects
the client to go to
https://www.google.com.
Summary
Opening port 80 on your firewall is no different than opening port 443, provided the web server is configured to redirect the traffic to a secure port. This also ensures users connecting on port 80 do not get connection errors.
