Synametrics Technologies
Revolving around the core of technology
IP Address Gets Blocked Due to Hacking Attempts
This article applies to Syncrify as well as SynaMan, which have built-in mechanism to detect if someone is trying to connect to the web server with a malicious intent. For example:
- Trying to send HTTP requests in clear when HTTPS is expected, or vice-versa
- Send invalid HTTP requests to determine how the server responds. For example, sending characters that could cause a buffer overflow.
- Try to use unsupported HTTP methods
In these cases, the server (Syncrify or SynaMan) will mark the IP address of the connecting client and will prevent that client from performing any task. Whenever an IP address gets blocked due to hacking attempt you may see the following line in the log file:
IP Address: xx.xx.xx.xx blocked due to previous hacking attemptswhere xx.xx.xx.xx shows the IP address of the offending client.
Why do I see the IP address of my own router/firewall
A problem arises when you see the IP address of your own router in this log. For example:
IP Address: 192.168.1.1 blocked due to previous hacking attempts
This happens if your router hides the IP address of the actual client connecting from the Internet. Since every client appears to connect from the same IP address, one misbehaving IP address will end up blocking every other client. Click here to see how to fix this problem.
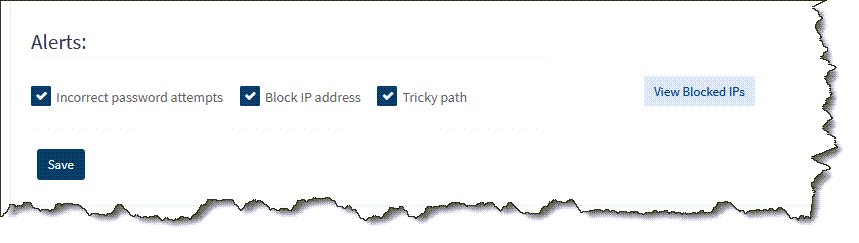
Viewing Blocked IP Addresses
- Log in as 'admin' from a machine that is not blocked, such localhost
- Click Configuration and select the Security tab
- Click View Blocked IP towards the bottom. See image below.
Can I do anything to prevent this in Syncrify?
Since the IP address of the connecting client is read from TCP/IP headers, nothing at the software layer can discover the actual IP address. Therefore, we strongly recommend you configure your router so it does not hide the actual IP.
You can certainly configure Syncrify/SynaMan to ignore the hacking attempts by adding:
block.blacklisted.hacker.ip=falsein server.properties file. However, this is NOT recommended for security reasons.
