Synametrics Technologies
Revolving around the core of technology
Failure Points
Administrators trying to run Syncrify, SynaMan or any other TCP/IP server often face difficulties configuring firewalls. This page discusses different network topologies that will help you identify failure points for your scenario.
Select a scenario from the list below that closely resembles your network environment. Each scenario represents a failure point, identified by FP[X] in the images below.
Scenario# 1: Inside your LAN
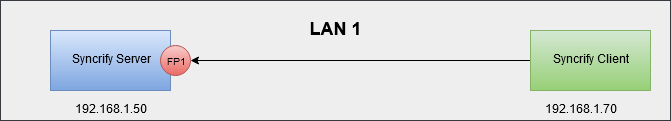
Possible Failure Points
In this case, both Syncrify Server and Syncrify Client are within the same LAN. The only firewall that should play a role is the local machine firewall where Syncrify Server is running.Scenario# 2: Inside your LAN through a VPN
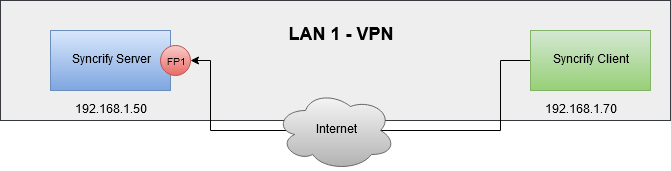
Possible Failure Points
In this case, a VPN makes a client running across the Internet to appear on the same LAN as the server. Most firewalls do not block any traffic passing through a VPN tunnel. Therefore, this is similar to Scenario# 1 from a software perspective and you need to ensure local firewall on the machine is configured correctly.Scenario# 3: Across the Internet
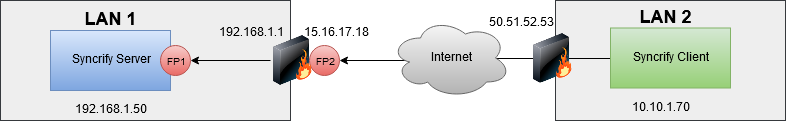
Possible Failure Points
This is the most common scenario when you want to use Syncrify across the Internet. Following key points should be kept in mind:- NAT (network address translation) is typically used on both ends. This means the client will connect to the public IP address of the server (15.16.17.18 in the image above) and the server will think client is connecting from 50.51.52.53.
- Two firewalls must be configured:
- Local firewall on the machine - FP1 in the image
- Network firewall on the edge of LAN1 - FP2 in the image
- Network firewall must be configured to allow ports used by Syncrify Server and forward the traffic to the machine where Syncrify Server is running, which is 192.168.1.50 in this example.
- Although not common, firewall protecting LAN2 could also impose rules on outbound traffic. These rules become more applicable if you're using non-standard ports for Syncrify Server. Often companies do not allow ports other than 80/443 to go out in order to limit and secure outbound traffic.
