Synametrics Technologies
Revolving around the core of technology
Password Protect your Emails with Encryption by Xeams
Most businesses' main form of communication is through email. In fact, according to The Radical Group Inc. about 128 billion business emails are sent each day. It's safe to assume some of these emails contain confidential and sensitive information, so what's to stop them from being seen by prying eyes?
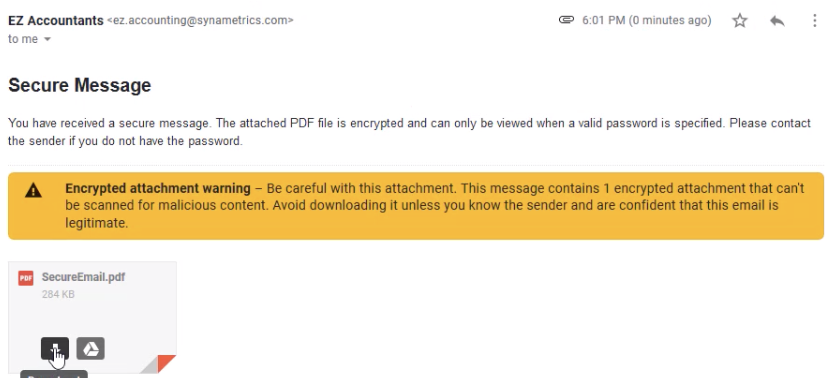
Consider a scenario where you are sending an email to a client. The message travels through several servers before it reaches the recipient. At every stage, there is a chance that someone may be looking at the message.
This means your message must travel through several different servers before it reaches its destination since there are no security measures in place to prevent someone from accessing that information.
For more information about End-to-End Encryption visit, http://www.xeams.com/how-to-encrypt-emails.htm
Xeams offers a solution to this privacy problem with End-to-End Encryption for outbound emails. End-to-End Encryption allows users to password-protect their emails, only allowing the intended recipient to open the email.
Why Should You Encrypt Emails?
There are several reasons:1. Privacy
The most important reason individuals and companies choose to encrypt their emails is privacy. As previously mentioned, about 128 billion business emails are sent daily. When information about business deals and finances are shared via emails, it is important that only those with the decryption key access them so that your company is not at risk for a takeover. No one wants their trade secrets to be revealed.
By encrypting emails, employees can ensure they are securing the integrity of an email and maintaining security by ensuring only the intended recipient will have access to an email.
2. Government Regulation and Compliance
While the United States does not have a unified privacy law adopted for the entire nation, it does have separate laws and guidelines governing most, if not all, government sanctions and industries where private and personal information is being shared. HIPAA, for instance, requires patient information to be confidential. Information is not to be shared without the consent of the patient. A hacker getting hold of patient information is a violation.Some other protection policies include:
CJIS - Criminal Justice System
GLBA - Banking Industry
FCRA - Credit Bureau
CFPB - Financial Industry
FERPA - Educational System
ECPA - 3rd Party Interception
Additionally, many countries worldwide have policies in place to secure data and personal information.
GDPR - EU
PIPEDA - Canada
APEC Privacy Framework - Asia
To ensure you and your organization are compliant with local and international government regulations and laws, it is essential you encrypt your emails.
3. Message Modification
Messages can easily be copied and modified in an email chain. For example, in the case of a middle-man attack, a hacker intercepts an email or other communication on the way to its recipient. The hacker can use this attack to impersonate one of the parties, misrepresenting them or even tricking the recipient into disclosing confidential information. The recipient would not be able to tell whether the email message which has been sent to him has been altered. With encryption, you can preserve the authentication of an email, as your messages will not be able to be tampered with.4. Identity Theft
In addition to privacy and message modification, you can prevent your identity from being stolen with email encryption. If any person gets hold of the username and password used to access your email account, they can read emails which as well as send false email messages on your behalf.This feature was also designed with a few other goals in mind. The recipient requires no other software to view your messages. This means you can send encrypted emails to anyone. Encrypted emails can be
accessed on mobile devices, and Internet access is not required to open the email. Lastly, there is no expiration date, and previous emails should never expire.

For more information about End-to-End Encryption visit, http://www.xeams.com/how-to-encrypt-emails.htm
If you would like to view a quick tutorial video on this feature, please visit, http://www.xeams.com/video-e2e-encryption.htm
Or contact out support team via
Email: support@synametrics.com
Phone: 609-750-0007
| Created on: | Oct 23, 2018 |
| Last updated on: | Jul 5, 2025 |
