Synametrics Technologies
Revolving around the core of technology
How To Avoid Malware Attacks On Your Business
Malicious spam campaigns have become more prevalent across multiple business communication channels in recent years. However, at the dawn of 2021, a new threat has been spreading which directly targets users of Slack and Basecamp. With these two outlets frequently being utilized by businesses, many large corporations are at risk of having spam compromise their day-to-day lives both in the office and at home.
The attacks work in two ways: The first targets employees working from home by infiltrating accounts on Slack and Basecamp to temporarily host malware and then deliver it to other targets listed on those accounts. The second campaign alerts users to be charged for an online service and requests a number be called. Upon calling, the operator will share a web link that will ultimately lead users to malware.
Research provided by Sophos illustrated how the first form of attacks were orchestrated by personalizing the recipient's name and company name embedded in the message. The manipulative tactic can easily persuade victims to open a message believing that it is coming from a reliable source with no risk preeminent. Inside the email, the messages contained a variety of claims, including information related to payroll, contracts, invoices, customer service inquiries, and even layoff notifications. The spam would be deployed as soon as victims attempted to open an attachment to the message.
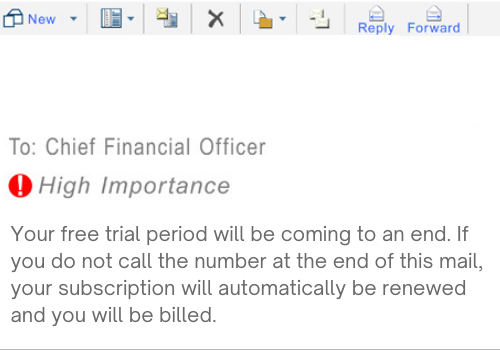
The second attack, now known as "BazarCall" sent out spam messages detailing a subscription or online service expiring and an urgent call would be necessary in order to ensure that a credit card was not charged for renewal. Those who would go on to call the numbers would be given a web link to "unsubscribe" from the service. However, upon visiting the page and clicking on the subsequent link, victims would be forced to open an Office document that would infect the device with malware.
Following a breached target, the hacker then injects the malware into the memory of a system process where it can go undetected. In this case, as a loader, the malware is capable of acting out several different devastating attacks against the entire system it has corrupted. The research conducted by Sophos predicts that malware like this is experimental and attempting new tactics to overtake businesses of prominence and high value.
In addition to this discovery, researchers have also seen a great deal of enhancements to the malware's features . For example, advancements like encryption can strengthen the malware's ability to remain undetected. Furthermore, a blockchain DNS service has also been discovered to prevent authorities from shutting down the domains that link to the threatening infrastructure. In the case mentioned earlier, the malware was distributed via email attachments and a fake internet link. Other instances in which malware can be distributed include fake internet ads, infected applications or websites, and pop-ups, which, when interacted with, can immediately install malware onto a device.
With this news and the imminent threat of more malware attacks on the rise, organizations big and small need to take malware prevention seriously. Many basic steps can be taken to avoid such a threat. Still, it is imperative to go above and beyond the basic security protocols to ensure that communications remain private and attacks are avoided.

- Deploying A Powerful Email Server: Many organizations may already have an antivirus or anti-spyware software installed. Still, additional security measures need to be deployed to ensure these messages never even make it into your inbox to begin with.
Employing a strong email server, for instance, can ensure communication remains private and secure with features like spam filtering and end to end encryption . A spam filter can prevent spam from entering your inbox, while end-to-end encryption can protect messages from the moment they leave your server until they reach the intended recipient unsuring no prying eyes gain access to private communication. - Multi-factor Authentication: While your email may already be password protected, it is imperative to deploy multi-factor authentication methods to enusre that your information does not become compromised. Using two-factor authentication is one method that can improve security by requiring a second form of identification before accessing information.
- Exercising Caution While Browsing & Using Email: Organizations need to emphasize the importance of cyber safety frequently. This includes having reoccuring meetings on the dos and don'ts of web browsing and email clicking. Having the right support on your side can help streamline this process. Once again, employing a strong email server can alleviate some of the stress of accidentally installing malware. Still, it is essential to do routine cybersecurity checks by carefully reading emails, avoiding calling mysterious numbers, and logging out of websites once you are finished.
Does your business lack the protection of a robust email security solution?
Consider checking out Xeams. Xeams is a secure and potent mail server for Windows, Linux, Solaris, MacOSX and other UNIX versions that support SMTP, POP3, and IMAP. The email server features a powerful spam filtering engine that eliminates up to 99% of junk email. By implementing Xeams, users can stop spam, viruses, hackers, and malware attacks while ensuring completely private communication.
Do you want to prevent intellectual property leaks while maintaining your customer-defined content filtering parameters? Give Xeams a try today for free! Check out the following link to get a free download: https://www.xeams.com/xeamsdownload.htm
| Created on: | Jul 20, 2021 |
| Last updated on: | Mar 9, 2026 |
