Synametrics Technologies
Revolving around the core of technology
Cryptolocker - How to avoid it and steps if you are infected
CryptoLocker is a ransomware trojan that
encrypts data files on infected computers and then asks for money should users wish to restore them.
Email is the most common mechanism for getting this type of virus, whose actual payload is often hidden. For example,
you can get an email containing:
- An executable file, with either .EXE, .COM or .SCR extension
- A zipped file containing an executable file
- An HTML file containing an IFRAME or JavaScript that automatically downloads the EXE file from a website
- A zipped file containing an HTML or a script file
If the user tries to open this deceptive PDF file, the virus starts executing by first encrypting files on the network drivers and then finally on the local computer.
Once files are encrypted, you will see additional files in every folder that is touched by the virus. The contents of a sample file are shown below.
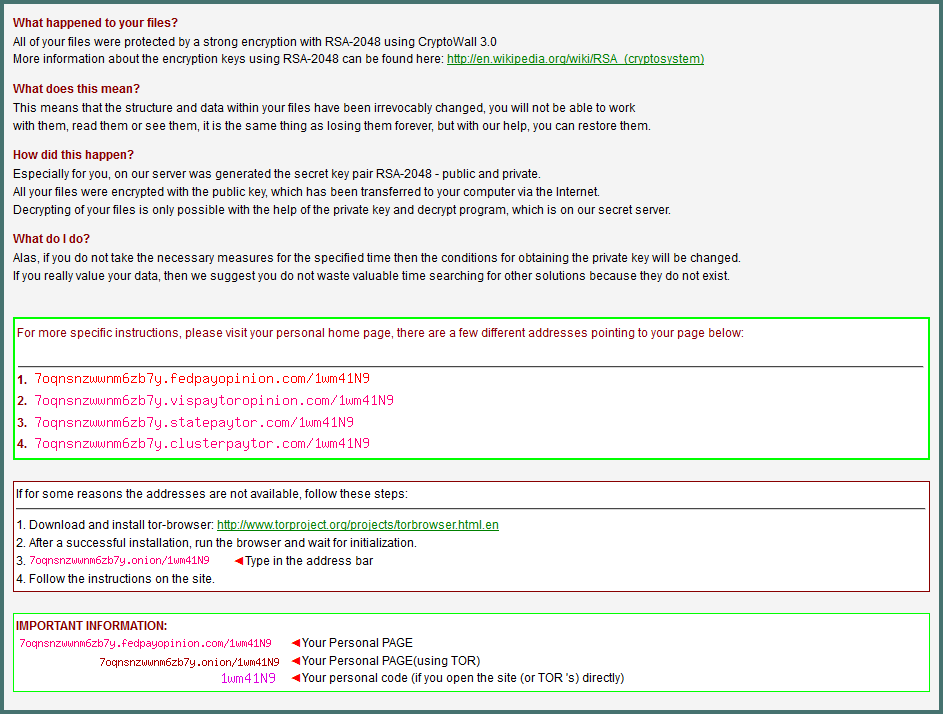
How to avoid getting CryptoLocker
A good email filtering solution, such as Xeams, is key to blocking such trojans. These email filters not only guard against suspected attached executables but also look inside a zipped file to ensure it does not have an HTML that would take the user to a malicious website.Xeams can be installed in front of your existing email server, such as Microsoft Exchange, with very minimal configuration to your actual mail server. It can optionally run in Firewall mode where it can monitor and filter emails coming in from the Internet and flag potentially dangerous emails.
Xeams comes built-in with several filters that can protect against emails containing malicious attachments. You can even configure it to use third-party virus detectors.
Prepare before it strikes
Another tool in your arsenal should be backup that allows you to go back a certain number of days, such as Syncrify. Many viruses are designed to stay dormant for some time, which makes it difficult to trace its sources. In such cases, a file-level backup works better than a disk-image backup. Click here to read more about how to decide the best backup for your needs.Among other features, Syncrify can create file versions of your documents. This way, should you be infected with a CryptoLocker, you can always restore files from a previous backup.
An interesting scenario could arise if a new backup overwrites previously backed-up data. For example, if you have a schedule to run backup every night and the virus attacks on a week-end, it is quite possible to lose even the backed up data. In such cases, versioning comes in handy. When restoring files, users can specify the number of days to go back. You can still restore files from a backup if you have versioning enabled.
Summary
Synametrics Technologies offer two solutions to fight against CryptoLocker virus.- Xeams - which blocks malicious emails from getting all the way to your inbox
- Syncrify - which provides a backup solution allowing you to restore your documents to a previous version.
| Created on: | Jun 26, 2015 |
| Last updated on: | Dec 20, 2025 |
